Enhance your systems' protection with PUF
Elevate your security effortlessly with PUF technology, where innovation meets unmatched protection

How our PUF technology creates trust with dynamic security
PUF (Physical Unclonable Function) technology leverages nanoscale variations during manufacturing process to create unique and unclonable digital identities .
When a PUF-equipped device is queried, it generates a unique responses based on its physical characteristics and intrinsic algorithms. These responses, used as a cryptographic seeds, keys or unique identifiers, ensure the authenticity, integrity and security of the device.
Consequently, PUF provides robust protection against cloning and tampering in addition to provide the best root-of-trust for secure applications layer.
The magic of PUF technology
in your USB keys, modules,
and standalone chips
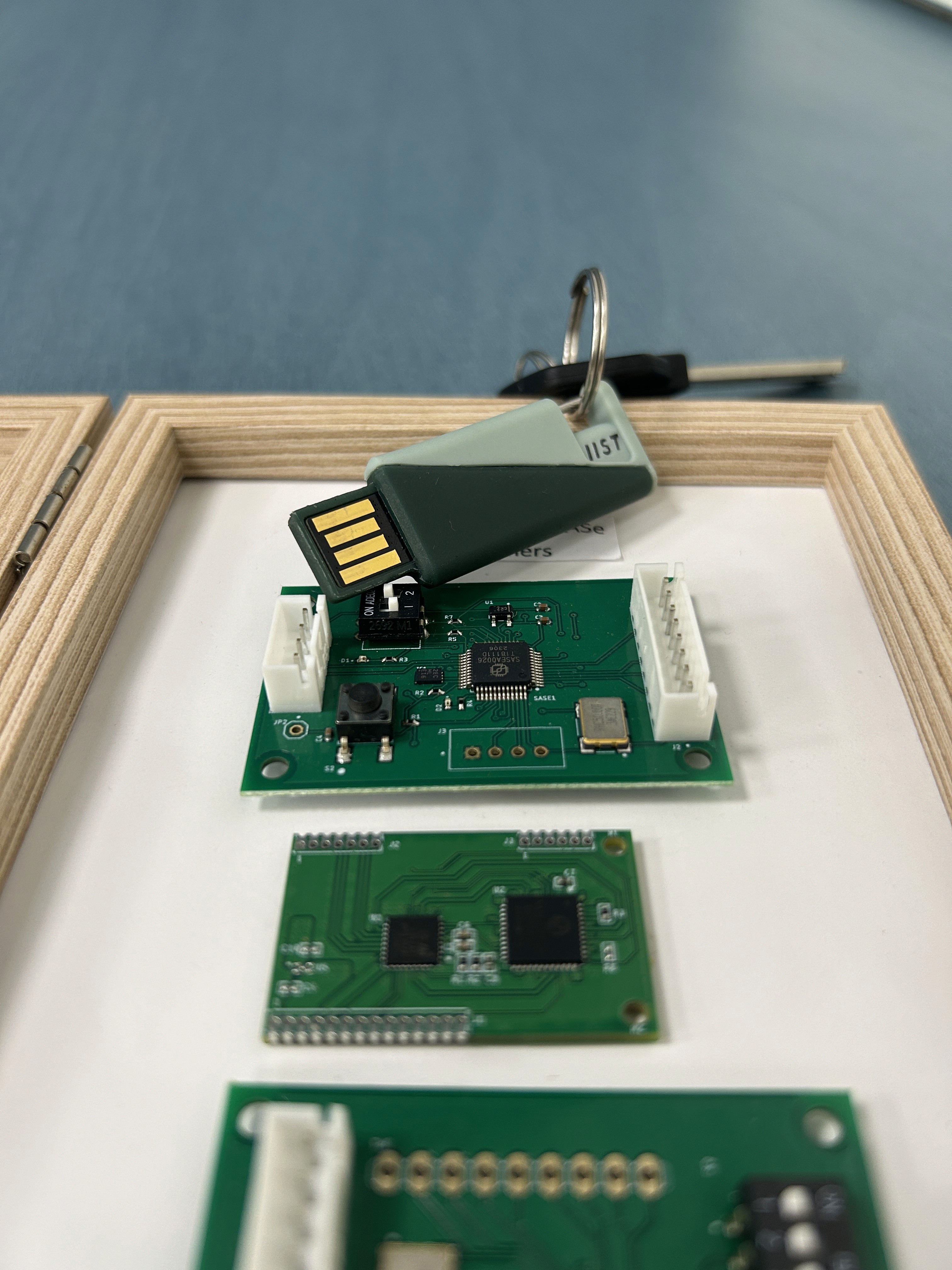
Achieve clear, impactful security with PUF technology in your USB keys, Embedded Systems and SoC

Standalone chips
IIST PUF standalone chips can be sourced separately and compatible with standards communication protocols to limit your product switching costs while increasing its security value.

PUF-enabled Modules
The modules are designed for integrators of electronics devices moving toward advanced embedded security. Our modules can be tailored to specific applications needs and requirements.

PUF security at your fingertips
USB keys with PUF embedded and FIDO2 compliant that provide unmatched security and reliable data protection wherever you go.
Our keys can be tailored to specific applications needs and requirements.
The Unclonable Identity: How PUF Works
Our Physical Unclonable Function (PUF) technology turns a chip's microscopic imperfections into its greatest security strength.
Ready for securing data and the Internet of Things
Discover how PUF technology can secure your data and the Internet of Things, providing a reliable solution tailored to your industry.
Join forces with us
for unmatched security with PUF Technology

Discover how PUF technology can secure your data and the Internet of Things, providing a reliable solution tailored to your industry.
NYCU-IIST R&D Center
NYCU-IIST Joint research Focused on hardware security technology development

Enhance your systems' protection with PUF
Elevate your security effortlessly with PUF technology, where innovation meets unmatched protection
service@iist.com.tw
FAQ
For any questions, check our FAQ where we've compiled the most requested information.